Projects

Gesture recognition using ambient light:There is growing interest in the research community to develop techniques for humans to communicate with the computing that is embedding into our environments. Researchers are exploring various modalities, such as radio-frequency signals, to develop gesture recognition systems. We explore another modality, namely ambient light, and develop LiGest, an ambient light based gesture recognition system. The idea behind LiGest is that when a user performs different gestures, the user's shadows move in distinct patterns. LiGest captures these patterns using a grid of floor-based light sensors and then builds training models to recognize unknown shadow samples. We design a prototype for LiGest and evaluate it across multiple users, positions, orientations and lighting conditions.
Download Papers: [IMWUT '18]
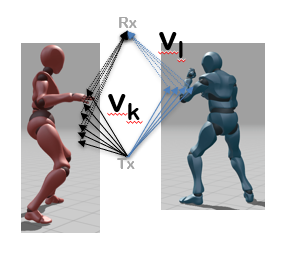
Multi-User Gesture Recognition Using WiF:WiFi based gesture recognition has received significant attention over the past few years. However, the key limitation of prior WiFi
based gesture recognition systems is that they cannot recognize the gestures of multiple users performing them simultaneously. We address this limitation and propose WiMU, a WiFi based Multi-User gesture recognition system. The key idea behind WiMU is that when it detects that some users have performed some gestures simultaneously, it first automatically determines the
number of simultaneously performed gestures and then, using the training samples collected from a single user, generates virtual samples for various plausible combinations of gestures. The
key property of these virtual samples is that the virtual samples for any given combination of gestures are identical to the real samples that would result from real users performing that combination of gestures. WiMU compares the detected sample against these virtual samples and recognizes the simultaneously performed gestures.
Download Papers: [MobiSys '18]
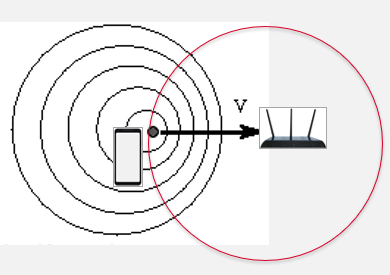
Enhancing Indoor Inertial Odometry with WiFi:Accurately measuring the distance traversed by a subject, commonly referred to as odometry, in indoor environments is of fundamental importance in many applications such as augmented and virtual reality tracking, indoor navigation, and robot route guidance. While theoretically, odometry can be performed using a simple accelerometer, practically, it is well-known that the distances measured using accelerometers suffer from large drift errors. To adddress this limitation, we propose WIO, a WiFi-assisted Inertial Odometry technique that uses WiFi signals as an auxiliary source of information to correct these drift errors. The key intuition behind WIO is that among multiple reflections of a transmitted WiFi signal arriving at the WiFi receiver, WIO first isolates one reflection and then measures the change in the length of the path of that reflection as the subject moves. By identifying the extent through which the length of the path of that reflection changes, along with the direction of motion of the subject relative to that path, WIO can estimate the distance traversed by the subject using WiFi signals. WIO then uses this distance estimate to correct the drift errors.
IoTm: A Lightweight Framework for Fine-grained Measurements of IoT Performance Metrics: Most Internet of Things (IoT) applications require unique guarantees on various performance metrics (such as latency, CPU availability, power fairness, etc.) from the IoT in-frastructure. A small deterioration in these performance metrics can cause serious violations of service level agreements. To ensure that the deployed IoT infrastructure delivers the guarantees on these metrics, the first step is to measure these metrics. We present IoTm, a framework for measuring IoT performance metrics, which include both IoT network’s quality of service (QoS) metrics and IoT node’s resource utilization (RU) metrics. IoTm has two key properties: 1) it is lightweight and thus amenable for implementation on resource constrained IoT nodes; and 2) it can perform measurements at fine-grained levels and not just at aggregate levels. IoTm is comprised of two components, a lightweight IoT node unit (INU), which resides in each of the IoT nodes, and a control and query unit (CQU), which resides in a logically centralized management server. The primary role of INU is to record appropriate information about the desired performance metrics in the IoT nodes. To record the information, INU leverages a generic data structure that we propose. CQU is responsible for identifying the metrics and the IoT nodes on which those metrics should be monitored to achieve a desired measurement objective. Application of this framework to evaluate Disk IOs and RTTs in an IoT node results in less than 5% error margin.
Download Papers: [ICNP '18], [IFIP '19]
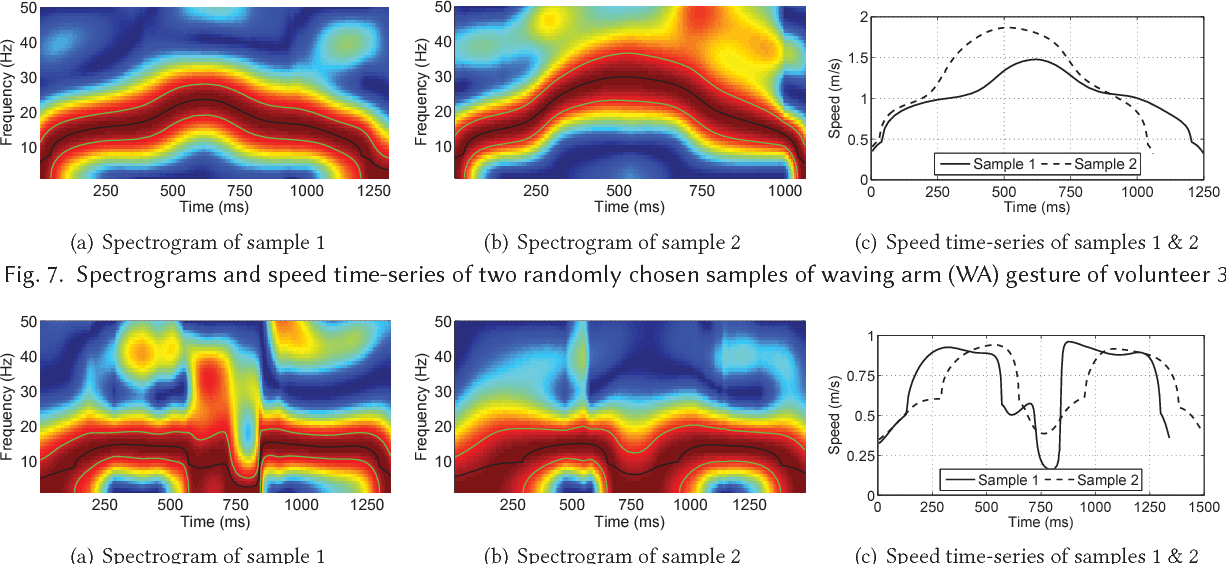
Augmenting User Identification with WiFi Based Gesture Recognition:This project proposes WiID, a WiFi and gesture based user identification system that can identify the user as soon as he/she performs a predefined gesture at runtime. WiID integrates with the WiFi based gesture recognition systems as an add-on module whose sole objective is to identify the users that perform the predefined gestures. The design of WiID is based on our novel result which states that the timeseries of the frequencies that appear in WiFi channel's frequency response while performing a given gesture are different in the samples of that gesture performed by different users, and are similar in the samples of that gesture performed by the same user.
This work is supported in part by the National Science Foundation, under grant # CNS 1565609
Download Papers: [IMWUT '18]
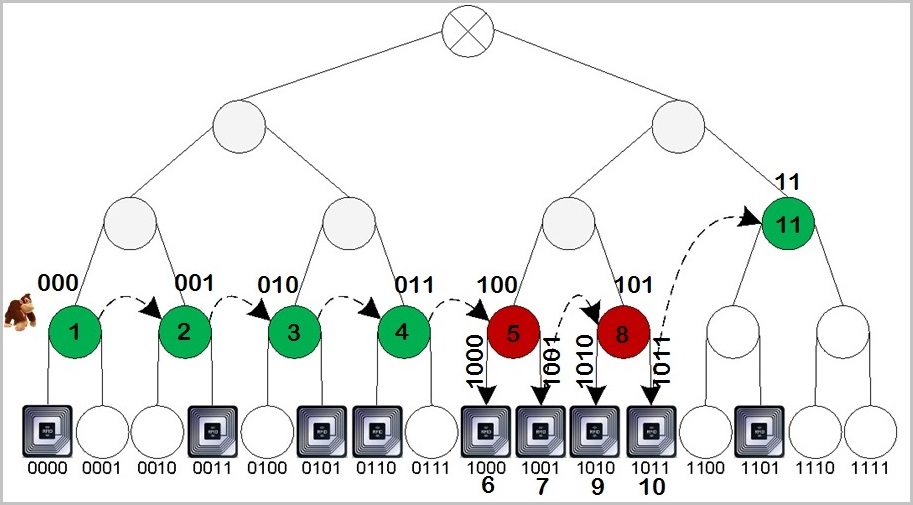
Tag Identification: An RFID system consists of tags and readers. Identifying RFID tags in a given tag population is the most fundamental operation in RFID systems. While the Tree Walking (TW) protocol is a well known protocol for identifying tags, little is known about its mathematical nature and only some ad-hoc heuristics exist to optimize it. In our work, we first analytically modeled TW, and then using insights from that model, proposed the Tree Hopping (TH) protocol that optimizes TW both theoretically and practically.
Download Papers: [ToN '14], [SIGMETRICS '13]
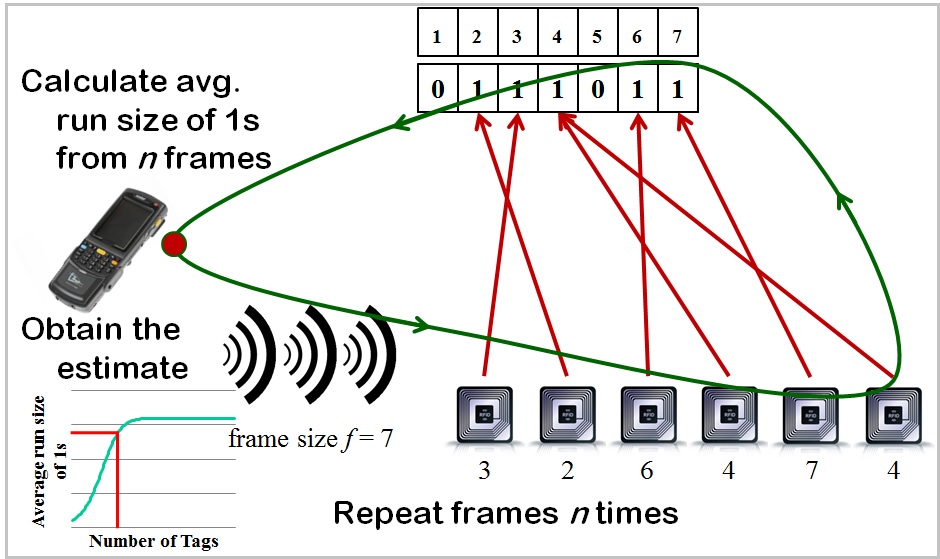
Tag Estimation: The second most fundamental operation in RFID systems is to quickly and accurately measure sizes of tag populations, called tag estimation. Tag estimation is needed in many applications such as privacy sensitive RFID systems and warehouse monitoring. We proposed tag estimation schemes to measure tag population sizes. The underlying technique is based on the average run-length of ones in the bit string received using the standardized framed slotted Aloha protocol.
Download Papers: [ToN '13], [MobiCom '12]

Missing Tags Detection: Shoplifting, employee theft, and vendor fraud are major causes of lost capital for retailers. RFID systems are deployed to monitor products by affixing them with cheap passive RFID tags and using RFID readers to detect and identify missing products. In our work, we take the first step towards addressing the problem of detecting and identifying missing tags in a population that contains tags with unknown IDs.
Download Paper: [INFOCOM '15]
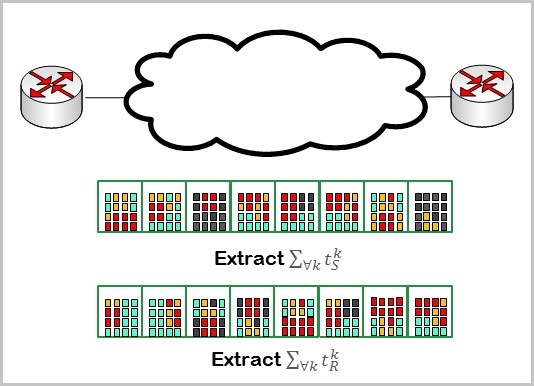
Network Metrics Measurements: With the growth in number and significance of the emerging applications such as high performance computing, data center networks, and financial trading that require stringent guarantees on network metrics such as latency, network operators are facing increasing need to accurately measure network metrics, especially on per-flow basis. Per-flow measurements are important because while network metrics may appear normal on aggregate traffic, they may be wildly abnormal for some flows due to mechanisms such as multi-path routing, DPI, and QoS. We proposed per-flow measurement schemes that neither interfere with network traffic nor attach auxiliary information to packets and at the same time achieve arbitrarily high accuracy using nominal storage and computational resources.
Download Paper: [SIGMETRICS '14]
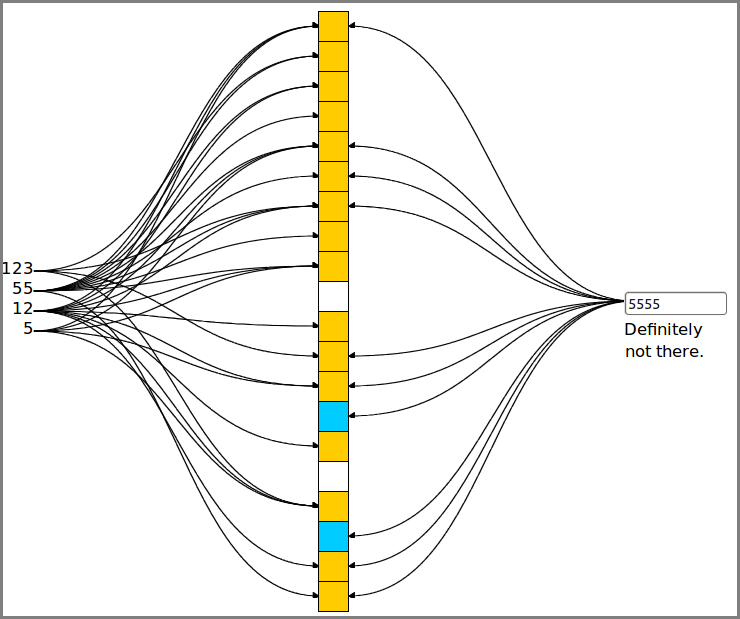
Network Set Queries: Network set queries such as membership queries (that check whether an element belongs to a given set), association queries (that identify the set among multiple sets to which a given element belongs), and multiplicity queries (that check how many times an element appears in a multi-set), are fundamental operations in network applications such as IP lookup, packet classification, web caching, and flow size measurements. We proposed a probabilistic network set query framework that can quickly process multiple types of set queries with guaranteed accuracy and without maintaining individual data structures for each type of query. At the same time, the framework is as simple in terms of memory and computation as a Bloom Filter.
[Paper Under Submission]
Network Protocol Modeling: Nature-inspired routing protocols such as AntNet, BeeHive, and DGA have received significant attention from researchers because they provide efficient, scalable, robust, fault-tolerant, dynamic, decentralized, and distributed solutions to traffic engineering within the existing connection-less model of IP. Despite these merits, due to lack of formal treatment, researchers have little formal understanding of the reasons behind good performance of nature-inspired routing protocols. Our work in this direction has focused on developing a formal framework to model and analyze nature-inspired routing protocols, which has enabled researchers to calculate the expected impact of different design choices on protocol performance.
Download Papers: [PPSN '08], [CEC '07]
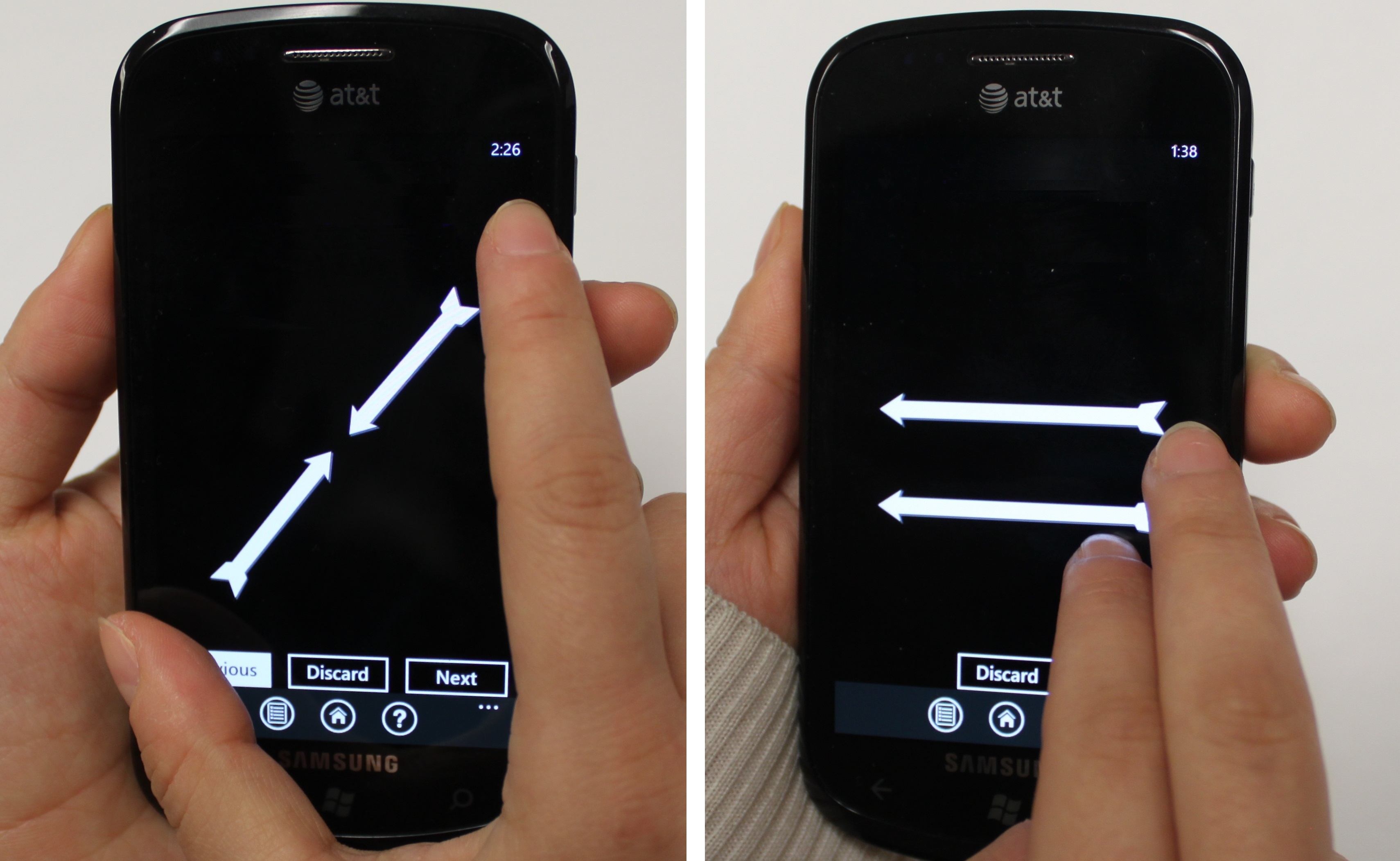
Behavior Based Authentication: Smart phones have become prevalent in our lives and often contain privacy sensitive information such as personal photos, emails, credit card numbers, and corporate data. One of the most important, imminent, and challenging problems in smart phone security is to design a secure and user friendly user authentication scheme. The widely adopted PIN/pattern based user authentication is susceptible to shoulder surfing attacks and smudge attacks. In our work, we developed a user authentication framework to authenticate users based on how they input instead of what they input.
Download Papers: [MobiCom '13], [RAID '09], [GECCO '09]
Download Demo: [Desktop version]
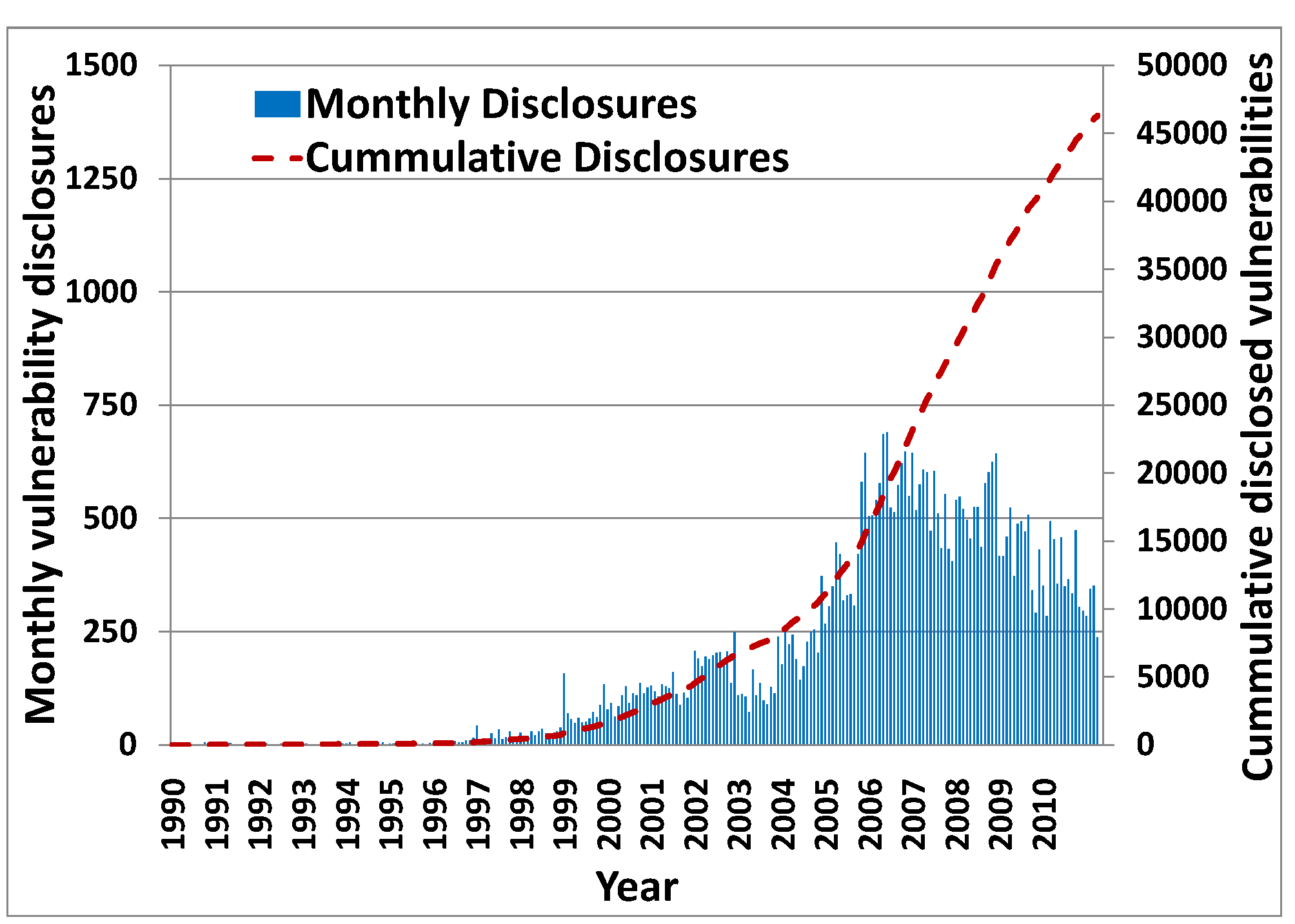
Software Vulnerability Measurements: Software systems inherently contain vulnerabilities that have been exploited in the past resulting in huge financial losses. The nature of software vulnerabilities is rapidly evolving; therefore, it is important to study various characteristics of vulnerabilities such as their severity, rates of disclosure, exploit and patch release, evolution of different types of vulnerabilities, and existence of common vulnerabilities in different products. We have characterized various aspects related to vulnerabilities and their life cycles to uncover interesting patterns for vendors and software products that are helpful in the deployment of best practices and security policies in the software development processes.
Download Paper: [ICSE '12]
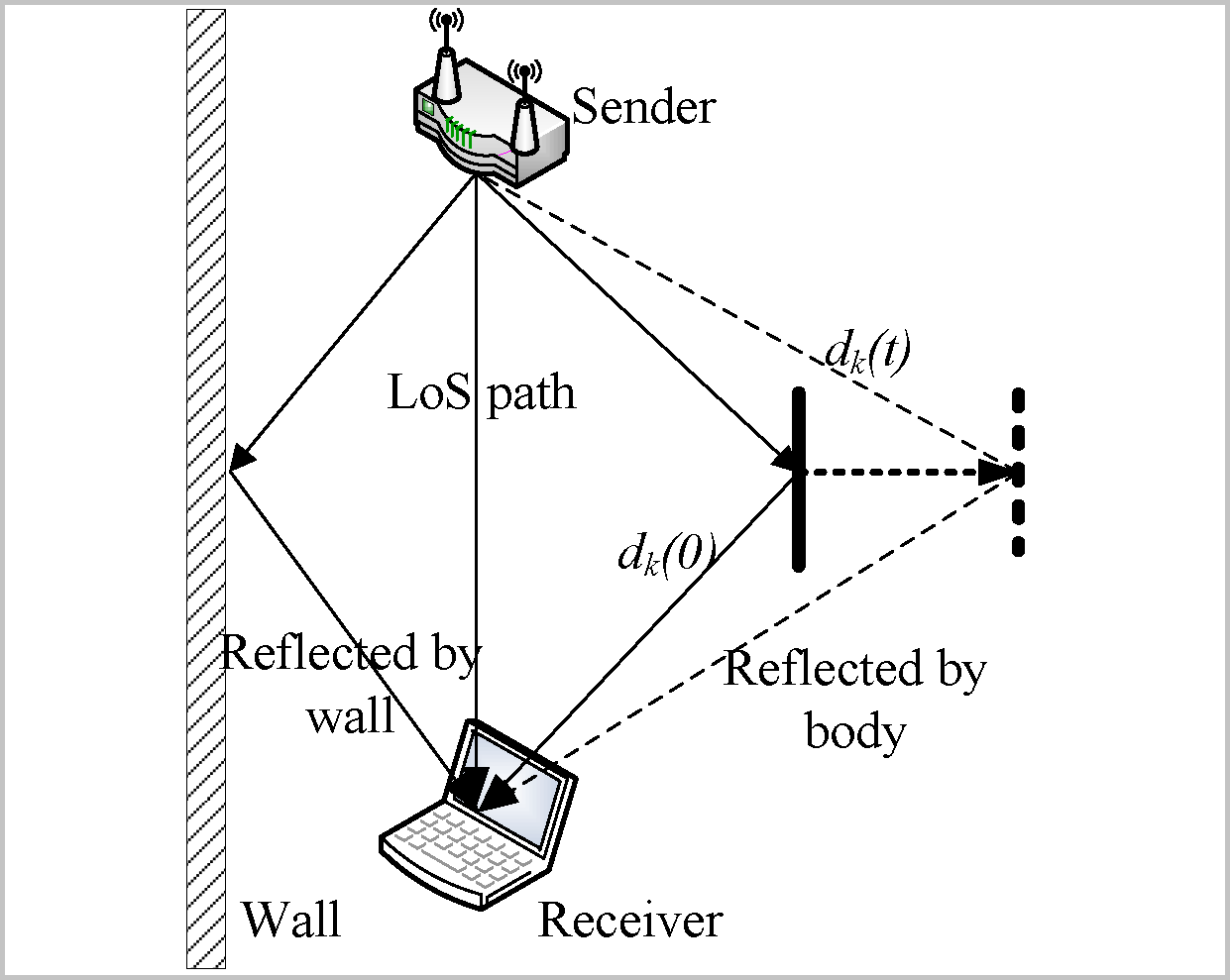
Activity Monitoring: Activity recognition and monitoring (ARM) is the core of a variety of applications that need to be aware of human activities such as building surveillance, smart homes, health care, and fitness tracking. Traditional ARM technologies either use cameras, which are not privacy preserving and need humans to continuously monitor video streams, or use wearable sensors, which are intrusive because users need to continuously wear sensors. In our work, we have proposed privacy preserving and non-intrusive schemes that use new sensing modalities including WiFi signals and ambient light for ARM. We have implemented our proposed schemes on prevalent devices such as laptops, which already have built in WiFi antennas and light sensors.
Download Paper: [MobiCom '15]

